The most flexible way to reduce risks
Cyber Inc. helps you and your organization to improve privacy and security awarenessor to take a first step. Are the technical measures sufficient, what responsibilities do the employees have and what awareness measures are imposed by standards and legislation and regulations? Together we map everything and make a plan to reduce the security and privacy risk
Cyber Inc. creates privacy and security awareness content for the online courses, such as videos, e-learning modules and tests for its own 2LRN4 platform that is specially made to make users aware of privacy and security risks. Every year we create more than 50 awareness activities. And we've completed more than 25 functional upgrades this year alone.
Let's take your security awareness to the next level!
Do you want to reduce security and privacy risks due to human error? We are ready to help you implement your privacy and security awareness program.
Trusted by companies

 hover/click me
check out how we help
hover/click me
check out how we help
 customers across
customers across
 Europe.
Europe.
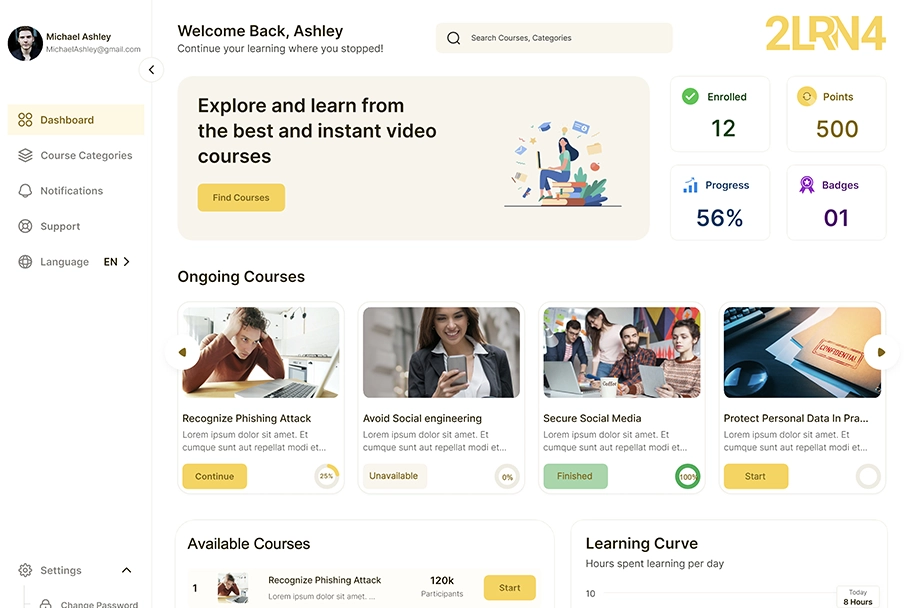
2LRN4 Security Awareness Platform
2LRN4 is a flexible, easy-to-use learning management platform (LMS), intended to help organizations improve their privacy and security awareness.
The platform has been developed in such a way that an organization can configure and manage everything itself, but that is not necessary. The platform is delivered including courses and is configured in such a way that adjustments are minimal.
Keeper Password Management
We'd love to show you how Keeper protects your organization's passwords, login credentials, and secrets with zero-trust and zero-knowledge security.
During the demo, we'll walk you through using the admin console to manage your environment. You'll also get a glimpse into the end-user Vault experience and discover how to set up advanced reporting and alerts. Additionally, we'll demonstrate how role-based access controls work and showcase the security audit view. Finally, we'll show you how the integration with AD/SSO works.
Phishing Simulations
With our template-driven simulations and tailored phishing, you can leverage existing phishing campaigns that have been tested and perfected over time.
Why reinvent the wheel when you can benefit from proven methods? Benchmark yourself against the most cunning phishing attacks out there and discover where your organization stands in the world of cybersecurity.